Crackme Solution 1 - Enter the House
I’ve always wanted to get into reverse engineering. I think it is really interesting and it makes you think outside of the box. At the same time, as a developer, it gives you insight on how an outsider may try to break your code whether it be for malicious or non-malicious purposes. Currently, I have knowledge in Java, Python, C, some basic MIPS Assembly, and some basic x86 Assembly. However, my knowledge in C is definitely weaker than my Java and Python knowledge. In terms of reverse engineering knowledge, I do have some knowledge of reverse engineering from emulating a popular MMORPG game known as MapleStory.
Anyways, I’ve decided I wanted to learn reverse engineering and to do so, I thought I’d get my hands dirty with some practice. I’ve decided to find some crackmes to solve. For my first crackme, I will be attempting a picture crackme by tay777 found here. I will be mirroring this crackme here in case the link dies for some odd reason.
Now then, let’s get started!
I will go step by step with my thought process.
First off, let’s figure out some hints to get us going:
-
It will be helpful to know what language this executable is written in, so we can possibly utilize knowledge of the language to find what we are looking for (ie. we are looking for a call to a comparison function or method). From the looks of the icon, I am suspecting it is a Visual Basic application. We’ll check this soon.
-
Looking at the hint.jpg, it gives us information on what windows are clickable and their position.
Now then, let’s load this up into a disassembler and see what is going on here. My disassembler of choice is IDA Pro. Unfortunately, the pro version is not free however you can get an evaluation copy here. You can also look into other alternatives. I think this post will come in handy. Note that the instructions below are written for IDA.
First off, let’s verify whether my guess of the language it is written in is correct. There are a few nifty ways to identify what language a program is written in. One way is to know a few functions or methods that you know are particular to a language (ie. strcpy, atoi in C). Another is to view the imports that a program makes. For now, let’s take a look at the imports. After scrolling through the imports a bit, I notice these:
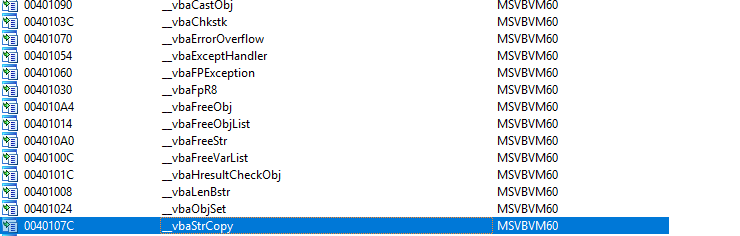
The biggest giveaways here are the functions that are imported are all prefixed with __vba (suggesting it is Visual Basic), however another way we can verify this is looking at the library that is being used. The library is MSVBVM60. With a quick Google search, we’ll come to realize this is from Visual Basic 6. Great! We are already halfway there. Now notice in the screenshot that I’ve also highlighted __vbaStrCopy. This could come in nifty. How about we look into that? Double clicking on this will bring us to something that looks like this:

This is just indicating that this function is being used in the program however it is actually coming from somewhere else (in this case, it is MSVBVM60.dll). We are interested in seeing where this function is being used, so I will x-ref (meaning jump up to whatever calls this). Hitting ‘X’ in IDA will show the x-ref prompt.
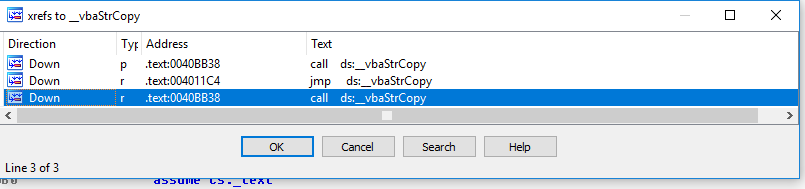
We are expecting the function to be called somewhere and a call instruction matches best. So we will look at the x-ref where a call instruction is being used. Following that x-ref, we will be at these sets of instructions:
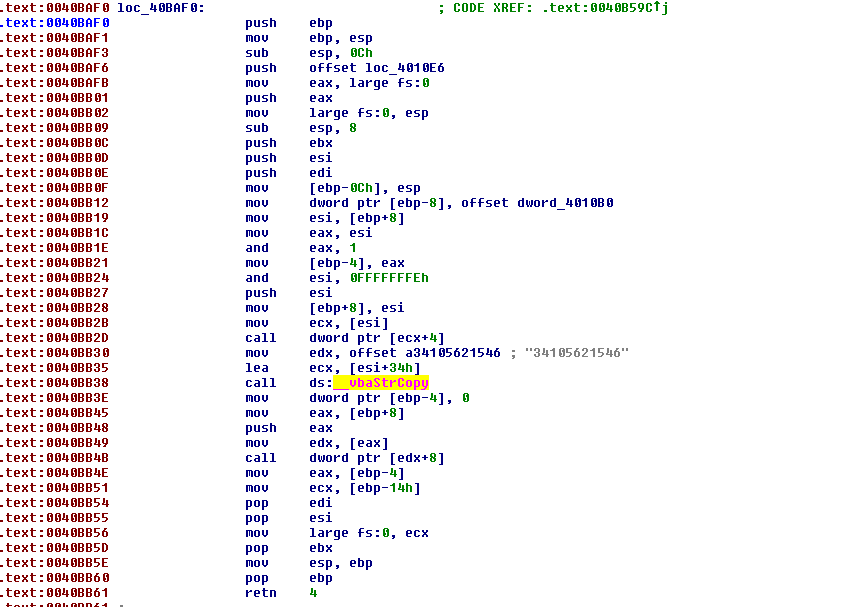
From the looks of it, the following instruction appears to be copying a string into a buffer of some sort:
mov edx, offset a34105621546 ; “34105621546”
We can however verify if this is correct by searching to see how __vbaStrCopy works. With a quick Google search we come across a page where someone has a documented this, you can find it here. Our suspicions are correct. But wait, what could 34105621546 mean?
Well, notice that each digit here matches a number from 0-6 (inclusive) which is exactly the number of positions for windows. And with a little bit of manipulation on our part, if you were to comma separate each value like so:
3, 4, 1, 0, 5, 6, 2, 1, 5, 4, 6
We can assume that this is the order in which the windows are to be clicked. Let’s try it and see.

Bam! We are in the house. Give yourself a pat on the back and go get some cake. 🙂